Well that was… …fun?
TL;DR; Updating SSL certs is a pain.

When checking my SSL certs, I discovered that with chromium based browsers this site worked. But Firefox decided that the certificate was not secure. It then gave you no options to, ‘I know what I’m doing please let me go there’. That would have then allowed me to check the certificate in Firefox to tell you what was wrong with it. Doesn’t this sound like something Microsoft would do as well?
So, i had to get the details from my CA server:
curl -vI https://jgt.me.uk
* Host jgt.me.uk:443 was resolved.
* IPv6: (none)
* IPv4: 194.164.95.67
* Trying 194.164.95.67:443...
* Connected to jgt.me.uk (194.164.95.67) port 443
* ALPN: curl offers h2,http/1.1
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: /etc/ssl/certs
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (OUT), TLS alert, unknown CA (560):
* SSL certificate problem: unable to get local issuer certificate
* Closing connection
curl: (60) SSL certificate problem: unable to get local issuer certificate
More details here: https://curl.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
So, there’s a problem.
I then had to log onto my plesk instance and the WordPress section, which told me nothing. Going to the ‘domains’ section allowed me to get to the server hosting it. Via the “SSL /TLS Certificates” button, I could finally see that… …There was no issue!
Well, at least as far as plesk was concerned.
It turns out that the The leaf certificate was ok. But the intermediate certificate from ” GeoTrust TLS RSA CA G1″ was not included.
Therefore, curl cannot validate the trust chain even though chromium based browsers like Chrome might accept it by filling in missing intermediates from their own stores.
So, I needed to regenerate the jgt.me.uk cert.
Could I find it on the 1&1 IONOS site? Could I heck! This is despite using them last time to generate it.
Ok, so I used one of the spare ones in my “Geotrust QuickSSL Premium”. IONOS seem to be really focused on trying to make me spend more money with them. Almost every time i click on something it results in a “Do you want to buy this”:
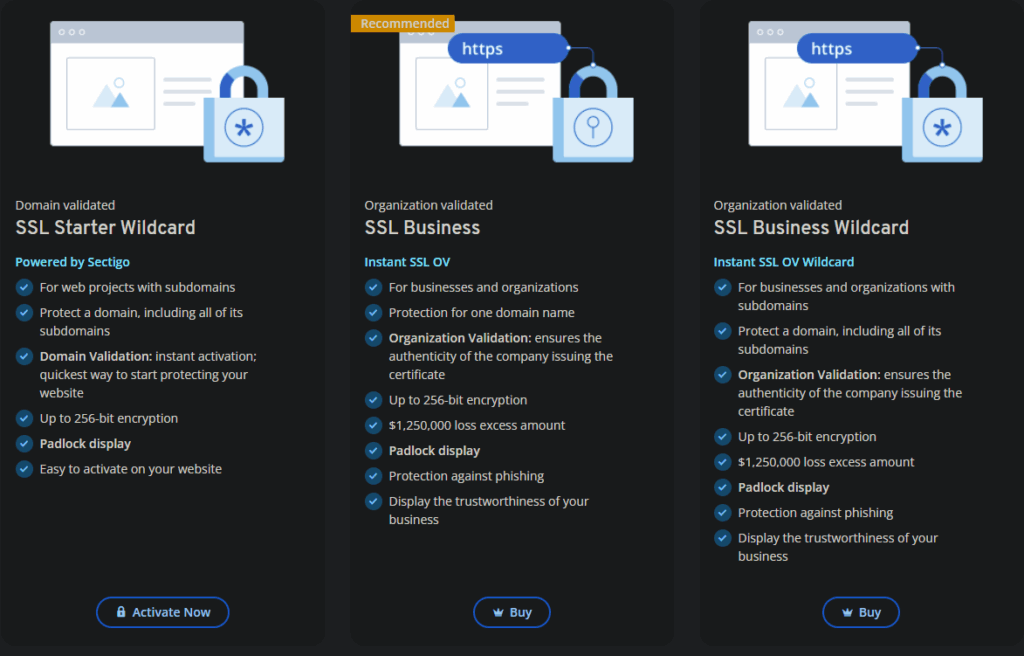
Note that the “Recommended” is the one that asks you to shell out more cash to them.
So when you ‘Activate’ you get the choice to download the private key.
You’re then taken to the SSL Certificates page to download your crt and intermediate certs. No problem there either.
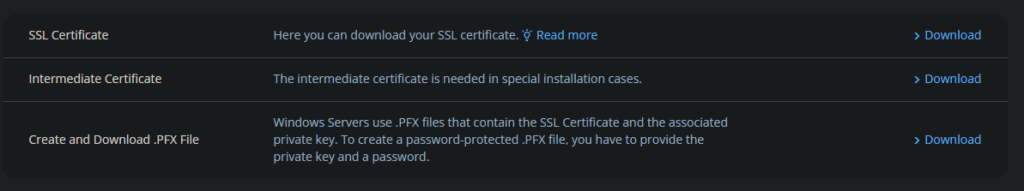
The fun starts when you try to use this certificate in plesk after removing the old one:
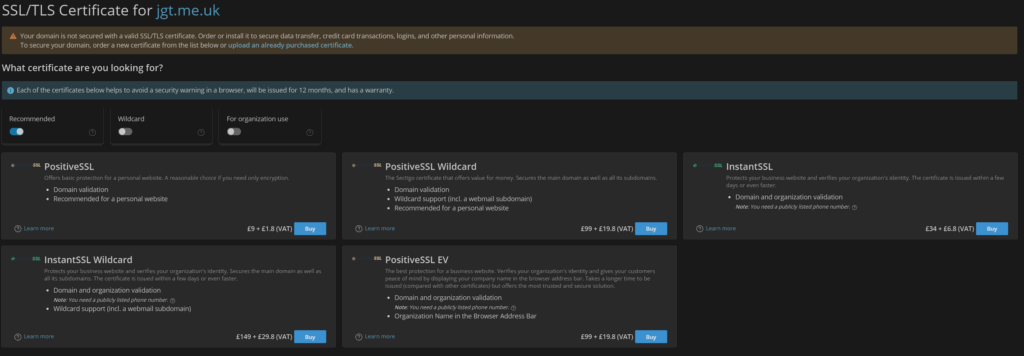
What the Heck?
You used to be able to chose something from the SSL Cert store in Plesk from that screen but now all you get is “buy something!”
The observant among you probably are saying, ‘but there’s a “Upload Already Purchased Certificate” ‘ option. Correct:
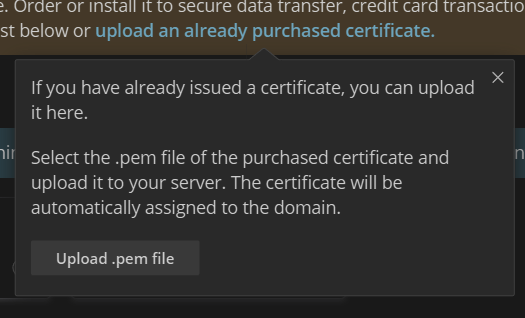
A .pem file, really? They don’t even tell you what’s expected in the file.
After a bit of trial and error, you need to use:
- Your
.key - Your
.cer - The
intermediate1.cer - And
intermediate1.cer
All mashed up together and that’s your .pem file. I suppose if you’re doing this all the time you should probably know this, but I only do this once a year. (see: https://docs.progress.com/bundle/datadirect-hybrid-data-pipeline-installation-46/page/PEM-file-format.html ) for an example.
After you have done this, and no got a working certificate, you then can use the ‘Advanced’ button to add that certificate to the site’s SSL store.
I suppose its my fault for assuming I needed to remove the cert before I could add a new one.
Anyways, its all working again.
‘Til next year.
This was written to vent a little over how annoyingly difficult something seemingly simple like renewing your own certificate can be. If it’d used “Let’s Encrypt” (like I do for many of my other hosted sites), I would not be writing this!
